The following content was written on March 31, 2020. Any new information since that date may not be included in this article.
Micah Lee and Yael Grauer did a great write-up for The Intercept outlining the different ways data can be encrypted, how Zoom’s use of the term “end-to-end encryption” doesn’t seem to align with the commonly accepted definition, and the possible ways this could affect the growing number of remote workers. Given our team’s experience developing a truly E2E encrypted alternative to Zoom, we’d like to add our perspective to their summary.
What Is End to End Encryption?
“End-to-end” refers to the “endpoints” involved in a data transfer, such as the sender and recipient of an email or two participants on a phone call. When data is encrypted end-to-end, the two endpoints are the only parties capable of decrypting it, which prevents man-in-the-middle attacks.
When it comes to conferencing, the number of endpoints is dictated by the number of participants. For example, a five-person video conference has five people sending and receiving video streams.
Is Zoom Communication Encrypted? How Zoom Meetings Handles Video Conferencing Encryption
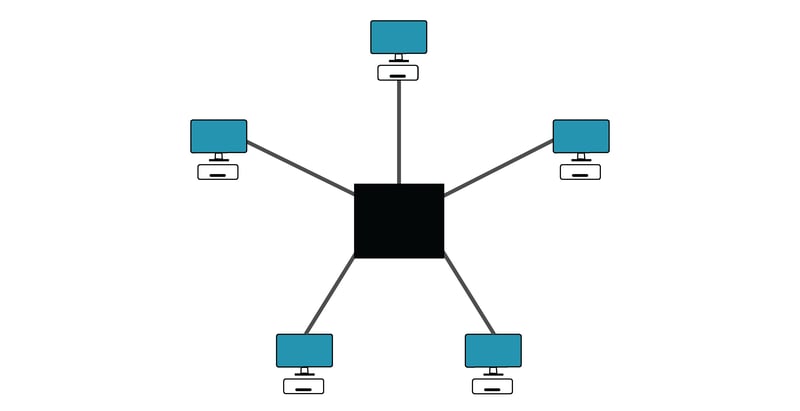
Service providers such as Zoom typically situate themselves in the middle of the group so that everyone sends video of themselves to a server and then that server packages them all together and sends that package back. In this regard, the service provider is treated as a trusted man-in-the-middle among the participants.
The trouble with the language in Zoom’s claims is that they seem to be framing their server as an endpoint, rather than a midpoint. Essentially, your video stream is encrypted from your computer to Zoom’s server, and it’s encrypted from Zoom’s server to the other participants, but Zoom has the tools to decrypt it in between.
If you give all of Zoom’s employees the benefit of the doubt that they follow the company’s privacy policy, this may not be cause for concern for your business. But you should understand that a backdoor may exist that could possibly allow a third party to enter.
The likelihood of the government or a hacker gaining access to Zoom’s decryption credentials is likely low for your business, but it’s a possibility you can avoid entirely with another service provider.
How OnSIP Achieves End to End Encrypted Video Conferencing
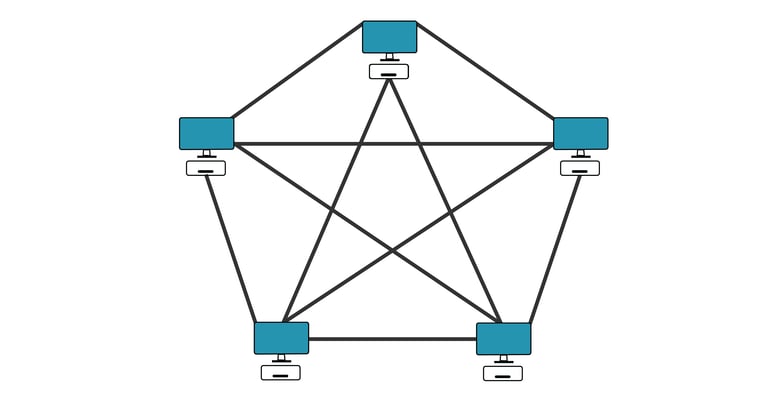
When we first began work in 2016 to expand our video calling platform beyond one-to-one calling, we made the decision to abandon the traditional method of facilitating video streams through a central server. Instead, we adopted a “full mesh” approach in which each caller has a direct one-to-one connection with every other caller.
OnSIP hosted PBX handles the setup and cleanup as callers join and leave but has no access to the audio or video content of the calls. Everything is encrypted and only the callers have the ability to decrypt it, which is done automatically by the app.
It may seem strange, but when you’re in an OnSIP video conference with four colleagues, you’re not actually entering a “room.” Instead, you’re engaging in four simultaneous one-to-one calls, displayed alongside each other. Since you can hear everyone and they can all hear you, you have the illusion that everyone has joined a central meeting room.
Clarity in Advertising Encryption
We should be clear: We don’t mean to imply that Zoom’s intentions are malicious—that their software was designed with snooping in mind or that their advertising is intentionally misleading. They don’t exactly have a spotless reputation, but this certainly wouldn’t be the first time a marketing department came up with an easily digestible adjective only to learn it had already been coined by the cryptography community for something meaningfully different.
SpiderOak, a company that offers encrypted file storage, among other services, put out a statement in 2017 acknowledging that their use of the term “Zero Knowledge” (to describe their inability to monitor their users’ uploads) did not fully satisfy the definition already ascribed to the phrase. They apologized to journalists and experts they may have misled and have used the phrase “No Knowledge” ever since.
Make an Informed Decision About Your Data Encryption Preferences
The point here is that everyone—service providers, users, journalists, experts—should have a common understanding of how potentially confidential data is being handled and by whom. “End-to-end encryption” shouldn’t mean one thing when spoken by a salesperson and another thing when spoken by a security expert.
When buyers are given a clear picture of their options, they can make an informed decision. Some companies may be willing to forgo end-to-end encryption in order to gain features that otherwise might not be offered (e.g., enlarging the stream of the person who spoke last, virtual backgrounds). In this environment where everything is becoming more and more digital, people are either caring less about their privacy or caring much more about it. If you fall into the latter group, you should know you have options available to you.