Firewalls are excellent security tools, and luckily, most devices have them built in. They’re by no means a be all and end all security solution, though. It’s important to know what a firewall can do as well as what it can’t. Firewalls are not the same as anti-virus software, but they are the gatekeeper for traffic to and from your network. They inspect incoming data packets and flag malicious ones. Or if an IP address outside of your LAN is getting too nosy, the NAT firewall in your router blocks it.
There are two types of firewalls: hardware and software. Hardware firewalls are part of your router. Not all routers, particularly if you use your ISP-issued hardware, have a firewall, or let you edit the settings. It’s worth checking! The hardware firewall is like the outer defense wall before you fall back to the keep (aka device-specific software firewalls). It protects your entire network at the first connection point.
Software firewalls are almost always built in to your device but aren’t necessarily enabled. Apple in particular has an application firewall that lets you change firewall settings for each app installed.
In short, firewalls are good, but there’s a bit of work required to make sure yours is working exactly as you want it to. Read on for firewall best practices and device-specific help.
Firewall Best Practices
Layered security is your best bet, always. Even if you do have hardware firewalls in place, don’t skimp on the software side. As we mentioned before, nearly all devices have firewalls in place already—it’s just a matter of turning them on and configuring settings to make sure nothing you want is blocked from coming in or out. Firewalls should block most remote access, but the keywords here are “should” and “most.” It’s difficult to tell, particularly for the average person, if you have a virus or someone accessed your machine remotely. That’s why outgoing firewalls are important: They can help detect malicious packets going out of your network from your device.
As an extra step, there are third-party firewalls available that add more security layers to your activity. It’s like using a VPN when connected to free WiFi: Extra security never hurts. (P.S.—you should make sure your firewall is up and running when using free WiFi as well.)
There are also times you might want to turn your firewall off, like if you’re gaming and connected to multiplayer modes or if the firewall interferes with your antivirus software. Just don’t forget to turn it back on when you’re done!
Setting Up a Firewall
No matter your device or operating system, you should be able to find your firewall settings very easily. It should come as no surprise—you find firewall details in your general settings privacy and security section.
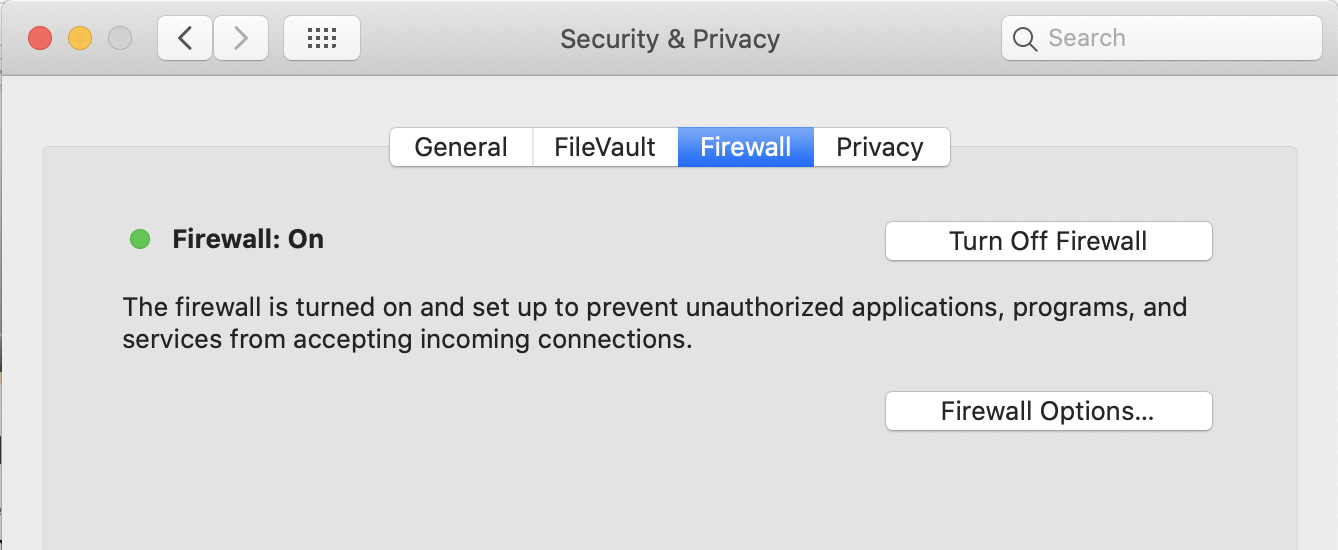
Apple’s Application Layer Firewall (ALF), which we mentioned earlier, takes some legwork in terms of time if you use a number of Internet-connected apps. On the bright side, Macs are pretty buff in terms of built-in security: Their detection rate is nearly twice that of Windows machines. You can enable the Mac firewall by going to System Preferences > Privacy & Security and clicking the Firewall tab.
For iPhones, it’s important to note that the built-in firewall only works when browsing on Safari. This is one instance where a third-party firewall comes in handy! There are two main choices for iPhones: Guardian and Lockdown.
Microsoft firewall settings are found through Start > Settings > Update & Security > Windows Security > Firewall and Network Protection. However, if you want to create specific firewall rules, you’ll want to read this.
Before we close out, we’ll just leave you with one more reminder. (And yes, we will drill this into everyone’s brain we can reach.) There is no single cybersecurity solution. Your devices have protections built in, but never assume they’re working at top capacity or enabled at all. Be like an onion—protect yourself with layers!