Every day, cybercriminals scan the digital landscape for easy targets—and small to medium-sized businesses top their shopping list. Why? You hold valuable data but often lack the robust security infrastructure of larger corporations.
The reality is stark: cyberattacks drain resources, disrupt operations, and damage reputations in ways that can take years to repair. This guide breaks down why your data matters to hackers, what they actually do with stolen information, and most importantly, how to defend yourself before you become another statistic.

Why Are Hackers After Your Data?
In today's digital economy, your data isn't just valuable—it's the prize. And the threat landscape has intensified dramatically.
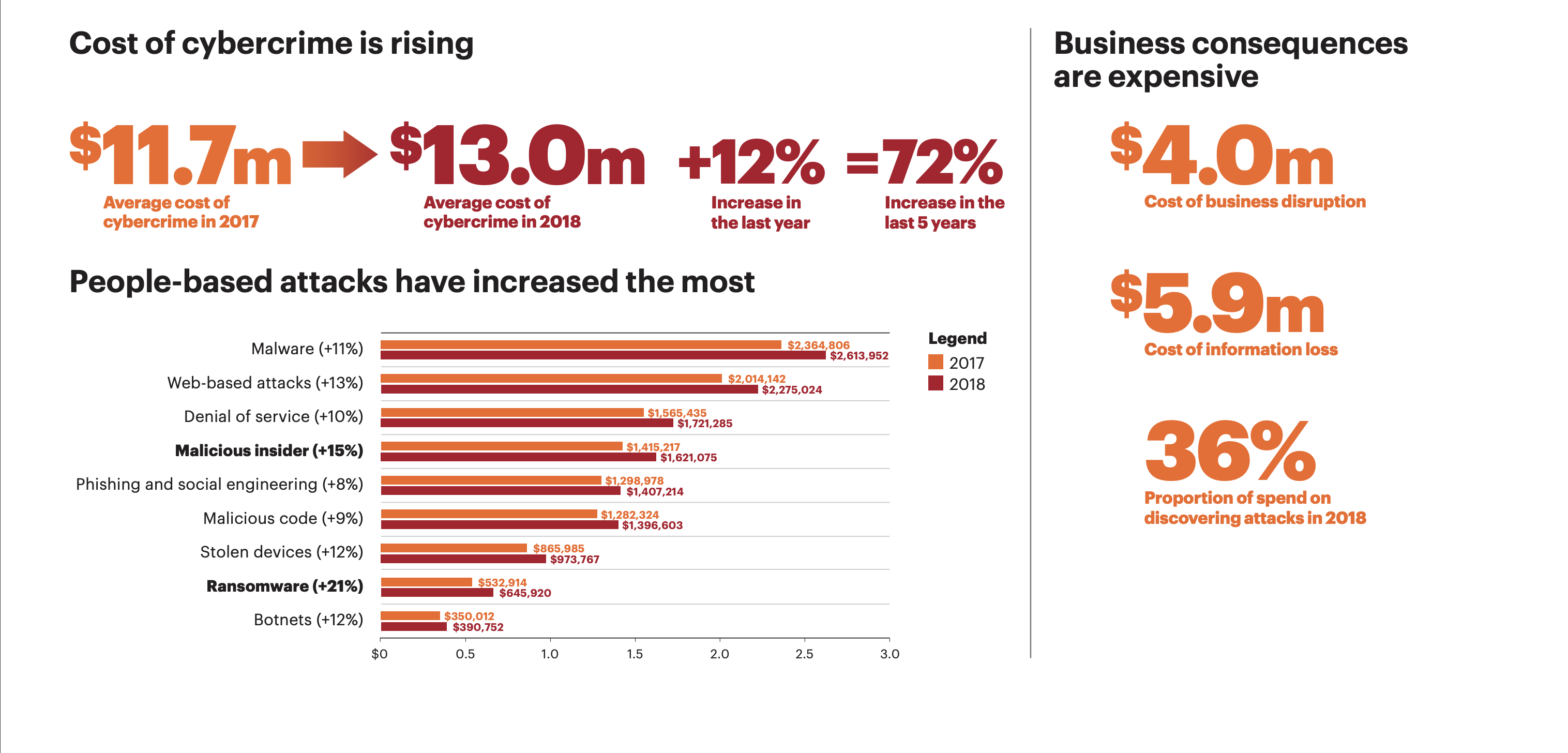
Consider the numbers: Between 40% and 72% of SMBs reported experiencing cyberattacks in 2024-2025, with some studies showing that 43% of SMBs have faced at least one cyber attack in the past year.
If you think you're too small to matter, think again. Roughly 70% of all ransomware attacks target smaller firms, with attackers knowing that SMBs can't pay millions but will pay a few thousand.
The human factor remains the weakest link. A 2024 study found that 49% of employees reuse the same credentials across multiple work-related applications, and 36% use the same credentials for both personal and work accounts. Meanwhile, 82% of breaches are caused by humans, whether through phishing, credential theft, or manual errors, and 65% of SMB employees bypass cybersecurity policies to make their work easier.
The attack vectors are evolving too. Over 3.4 billion phishing emails are sent every day in 2025, and the FBI's 2024 Internet Crime Report documented 193,407 phishing and spoofing complaints resulting in over $70 million in losses. AI has supercharged these attacks, enabling cybercriminals to create highly realistic impersonations that even security-conscious employees struggle to detect.
Cybersecurity for Beginners: What Do Cybercriminals Do With Your Data?
They sell it, most likely, or publish it on the deep web. Or they lock it and hold it for ransom. The type of damage hackers or their buyers inflict with stolen data depends on the type of information stolen. Eventually, it’ll end up on an underground market.
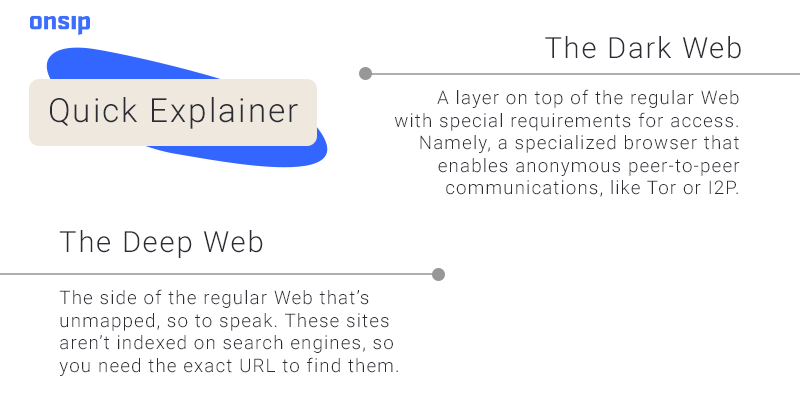
Personal Identifying Information (PII)
Think: Name, birthday, SSN, phone number.
If it can identify, locate, or contact you, it’s PII. Odds are, this is what hackers are looking for. As stolen information goes, PII is fairly malleable to a cybercriminal’s whims. They could apply for loans or credit cards and file fake tax returns in your name. Or they could subject you to a lifetime of spam. That’s a wide spectrum but one that’s aggravating across the board.
Financial Information
Think: Bank and insurance information, billing accounts.
Used to pay bills or transfer funds. Would you notice an extra couple of bill payments each month or if someone were skimming your bank account? The savvier cybercriminals could even make themselves credit cards in your name. Most of the fraudulent activities mentioned with PII apply here as well.
Payment Card Information (PCI)
Think: Your credit and debit card numbers.
While part of financial information, specific card details can result in immediate transfers or online purchases. It doesn’t take much time to rack up a hefty credit card bill on someone else’s dime.

Education Information
Think: Transcripts and school records.
True, this type of information is not as instantly lucrative as the others. Instead, it’s often used for blackmail and extortion. Fear works in the hacker’s favor here. Alternatively, they’ll pose as part of the school to phish you.
Healthcare Information
Think: Insurance and hospital records.
How much of your PII is listed in hospital records? With insurance information, cybercriminals can mess with your insurance by filing false claims and buying prescription meds in your name.
User Credentials
Think: Usernames and passwords.
If you regularly sign in with OAuth, imagine how many accounts you’re jeopardizing with one weak password. Consider your primary email login the Pandora’s Box of cybercrime. Some hacker rolls in and sets your inbox to auto-forward to her account. From there, she hits every “I forgot my password” button she finds. If your work email is compromised, she might spy on your company or attempt intellectual property theft. Think of all the PII stored in the average adult’s primary email—bank statements, rental applications, legal correspondence, and let’s not forget the contact list that’s grown unchecked since before Facebook had a timeline.
With such a data treasure trove in your inbox, it’s no surprise that phishing is the most recurrent attack vector. Read on for a rundown of the most common cyberattacks.
Common Cyberattacks
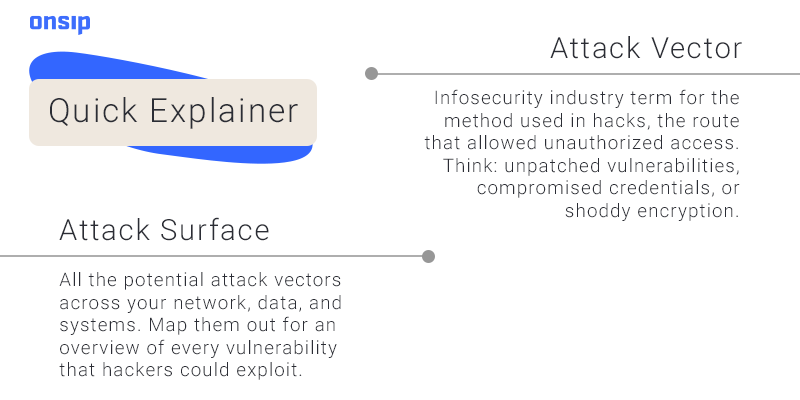
Zero-Day
Taking advantage of software vulnerabilities before they’re patched. Zero-day vulnerability is the actual hole in the software. The creators don’t know about it, and antivirus software doesn’t know to look for it. Zero-day exploit is the code attackers use to get in through the security hole. Famous Zero-day attacks: Stuxnet, the 2014 Sony fiasco, Adobe Flash for its entire existence, and of course, the DNC.
Phishing
Hackers send emails posing as reputable contacts—someone in your organization or a known brand—hoping to trick you into sharing information or downloading malware. Spearphishing is a targeted attack by the same methods, where hackers go after individuals with higher access or privileges. Vishing is phishing over the phone. Your voice confirms your PII, credentials, financial information, and more to the very reputable lady who was definitely calling from the bank. Smishing is similar but uses SMS instead of voice.
Trojan
Malware disguised as helpful software. Trojans might get to work at once or they could bide their time, which makes them particularly dangerous. How to handle Trojans: Don’t download or install anything questionable, from seemingly routine apps to your torrenting habit.
Ransomware
Hackers use malware to hold your files ransom. Businesses in particular tend to pay up because the cost of losing their files or having them published causes more than just financial damage. The catch: You have no idea if you’ll actually get your files back, if they’ll remain unpublished, or that the hacker hasn’t already deleted them.
Distributed Denial of Service (DDoS)
A Denial of Service (DoS) attack that uses multiple devices to launch. Hackers flood you with traffic to eat up bandwidth and resources. You have to scramble to fix it and go offline if you haven’t crashed already. Why hackers bother: It’s a favored revenge move and a useful diversion for hackers trying to break into your otherwise monitored system.
With so many types and methods of cyberattacks, maintaining your security can feel daunting on a good day. Fortunately, the key steps to personal and professional data security are simple.
The Future of Cybersecurity: 6 Ways to Protect Yourself and Your Business
The top attacks expected in the near future: phishing, ransomware, DDoS, and password-based attack vectors. Joining the top tier are compromised business emails and IoT- and AI-based attacks. We already knew that attacks on businesses are trending up compared to those on individual consumers, so the first additions shouldn’t surprise anyone. As for the latter two, both areas continue to rapidly grow with 5G expansion. As the IoT grows and AI development expands, so too do correlated cyber threats. Escalation is a constant in cybersecurity, and you should approach it accordingly. Here are some top ways to maintain and improve cybersecurity in your life:
1. Multifactor Authentication
Hopefully, you already use two-factor authentication for most secure logins. It takes a few seconds of your day and packs a heavy security punch. You’re already used to it! For those with access to sensitive business and client information, multifactor authentication is a simple way to add extra protection.
2. Education
You can’t protect your data or devices if you don’t understand the threats. It only takes one weak password to break a company. With business email compromise expected to rise, can you confidently say that every person in your organization follows the bare minimum in security practices? What about three months from now? Require cybersecurity training, and not just during new employee onboarding. Make it regular, make it thorough, and make sure your team actually pays attention.
3. Prevention Over Containment
Audit your network and website for weak spots so that you have a regular idea of your attack surface. Make patch management a priority. Put resources into a cybersecurity team that can supervise and enforce employee security protocols. Containment doesn’t help when the damage is done. Focus on prevention.
4. Default Security Settings
If it connects to the Internet, it’s hackable. If we haven’t scared you enough, Google “baby monitor hacked.” On how many of your smart devices have you actively checked and updated the security settings? Factory default settings are rarely strong. To help get you started, we have a guide to securing all aspects of your VoIP phone system.
5. Strong Passwords
We’ve said it before, and we’ll say it again. Use a password manager to generate strong passwords and organize them. All you need to do is remember one extremely strong password and you can access your vault.
6. Web Cautions
You should take some general precautions when surfing the Web, including the following:
- Avoid unsecured sites. If you don’t see a closed padlock on the far left of the URL bar, then get out. Need to secure your website? Here’s how.
- Don’t click suspicious links or download attachments from unknown email addresses. Don’t trust the name in your inbox—check the address.
- Limit the amount of personal information you share. It is stored, and it will be used against you. Even if you delete your Facebook account, your data remains on their servers.
- Use a VPN! A VPN creates a private network from a public Internet connection. Consider it your seatbelt for the Internet car. As in, it’s not the only safety feature you should have, but it’s one of the most important.
The Choice Is Yours—But the Clock Is Ticking
While the statistics are alarming, most breaches stem from preventable failures—weak passwords, unpatched systems, employees clicking suspicious links, and organizations that treat security as an afterthought rather than a foundation.
The good news? You don't need a Fortune 500 security budget to dramatically reduce your risk. The six strategies outlined in this guide are practical, implementable measures that work.
Remember: cybercriminals aren't looking for perfect victims—they're looking for easy ones. Every security measure you implement shifts you from the "easy" column to the "not worth the effort" column. That shift could be the difference between business continuity and becoming another cautionary statistic.