There’s cloud architecture, and then there’s cloud security architecture. The former is (almost) nothing without the latter, especially as the cloud service provider oligopoly continues to grow stronger. Fewer CSP options increase the risks for all businesses even as it makes life simpler in the immediate timeline. So it’s become imperative to build security into cloud architecture from the get-go rather than adding security features at the end.
Typically, that’s been the strategy—building out functionality and trying to fit in security at the end. But with cyberattacks continually rising and most of the world’s devices connected to one or another major cloud system, we’re seeing a shift in build priorities to finally bring security to the forefront.
What Is Cloud Security Architecture?
It’s too easy to think of the cloud as this noncorporeal, almost ethereal entity. But it’s not. It’s made up of all of our computers, servers, and more and more hyperscale data centers. That’s a lot of hardware with a lot of vulnerable entry points. There are numerous ways we can employ endpoint security:
- Use a VPN.
- Be aware of the dangers associated with free WiFi and public networks.
- Keep good password habits, like using a password manager.
- Stay updated on cybersecurity 101.
- Don’t trust websites without SSL.
The list could go on, but this blog is about cloud security, not endpoint security. We just like to throw in reminders any chance we get. Cloud security architecture comes down to a couple of main points: privacy by design and the shared security model.
Privacy by Design (PbD)
PbD is a design methodology around since the ‘90s that emphasizes the importance of building technology with security as the central focus. You may know other design methodologies like human-centered design (HCD), which emphasizes creating for the users’ needs rather than focusing on a product build that may look nice but will befuddle anyone trying to use it.
PbD emphasizes building around security from the start. Otherwise, as happens all too often, the priority is on the product’s functionality with security features tacked on at the end. When you try to retrofit security after the fact, it usually ends up subpar, which is no longer a viable option for cloud computing in particular (not that it ever was). Naturally, PbD and cloud security architecture go hand in hand. As nice as it would be, cloud security doesn’t end with the product build. It takes all of us all the time to keep it at peak performance.
Shared Responsibility Security Model
All cloud technology should have strong security built into it, but the buck doesn’t stop there. It takes each of us using the cloud to maintain security standards. Your security responsibility as a cloud user depends on the type of service you use: IaaS, PaaS, or SaaS. Each provider is different, so it’s up to you to negotiate the specifics of shared responsibility in your contract for clarity.
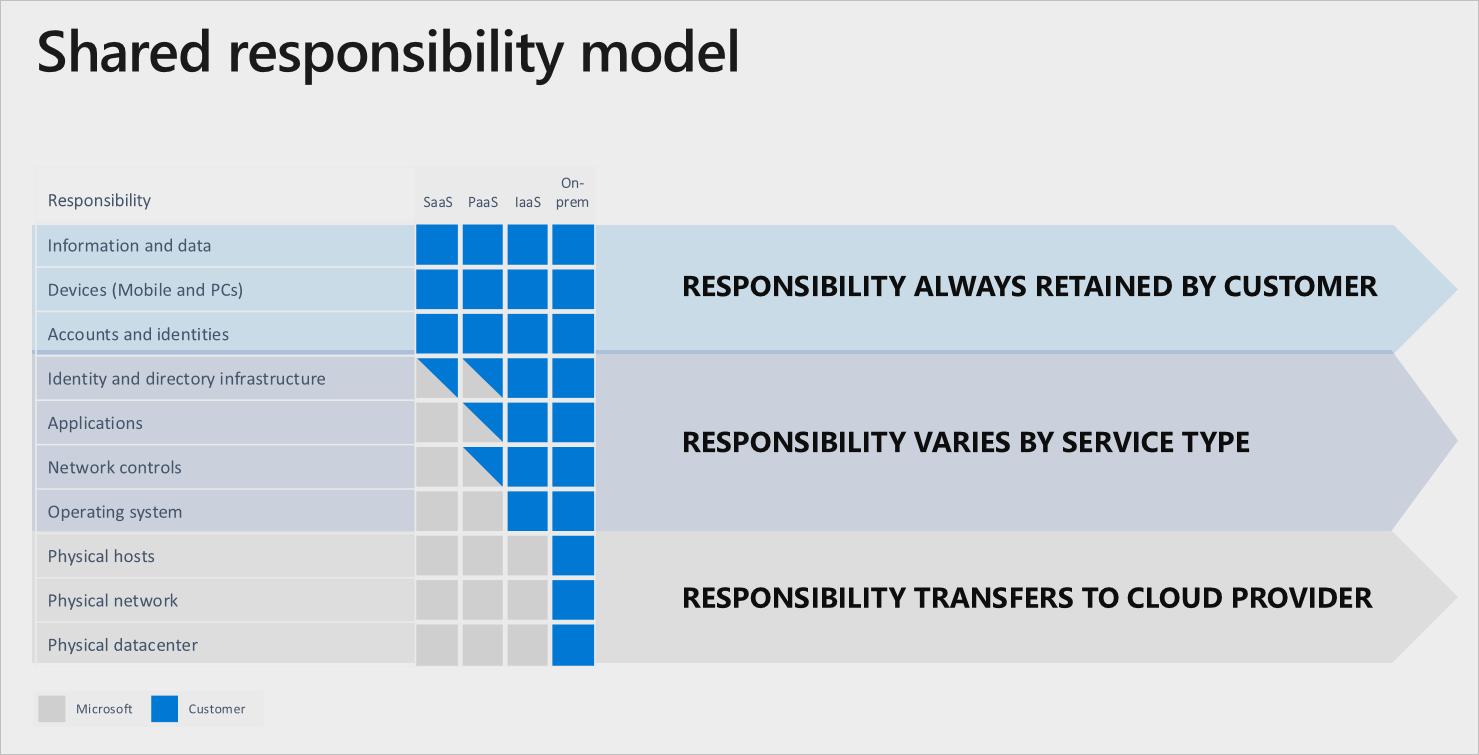
As the model shows, responsibility can vary greatly. In most cases you, the user, are still responsible for some security elements. This is where strong cybersecurity training at work comes into play as well as enforced habits like strong passwords and having liability agreements in writing.
The bottom line is to never assume your cloud service has security perfectly handled. Cloud security architecture should create a strong base, particularly if you choose the right cloud provider, but both cloud tech and cyberthreats constantly evolve, so it’s important to remember that you and everyone in your system are also part of that security architecture.