A Distributed Denial of Service (DDoS) attack represents one of the most disruptive forms of cyberattack facing businesses today. These attacks work by flooding your network infrastructure, websites, or online services with overwhelming amounts of traffic, effectively shutting down operations and blocking legitimate users from accessing your resources.
The Difference Between DoS and DDoS
While both Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks share the same ultimate goal—making your systems unavailable—they differ significantly in execution and impact.
A traditional DoS attack originates from a single source. One compromised computer attempts to overwhelm your server or network by sending excessive requests. While potentially disruptive, these attacks are relatively easier to identify and block since all malicious traffic comes from one location.
DDoS attacks are exponentially more dangerous. Instead of one attack source, DDoS leverages hundreds, thousands, or even millions of compromised devices simultaneously bombarding your infrastructure from multiple locations worldwide. This distributed approach makes these attacks dramatically more powerful and significantly harder to defend against.
The Alarming Growth of DDoS Attacks
The threat landscape has exploded in recent years. During the first quarter of 2025 alone, over 20.5 million DDoS attacks were blocked by major security providers—representing a staggering 358% increase compared to the same period in 2024. Looking at the full year 2024, DDoS attacks worldwide increased by 108% compared to 2023, essentially doubling in just twelve months.
How Botnets Power Modern DDoS Attacks
The secret weapon behind most DDoS attacks is the botnet—a network of compromised devices remotely controlled by cybercriminals. The term "botnet" combines "robot" and "network," and that's precisely what these are: armies of hijacked machines working in perfect coordination.
Here's the concerning part: these botnets aren't built from sophisticated computers in underground hacking labs. They're constructed from everyday Internet of Things (IoT) devices—smart home assistants, security cameras, routers, baby monitors, and even connected refrigerators. Each device gets infected with malware, often without the owner ever knowing. The attacker then controls this digital army remotely, directing all infected devices to simultaneously target your infrastructure.
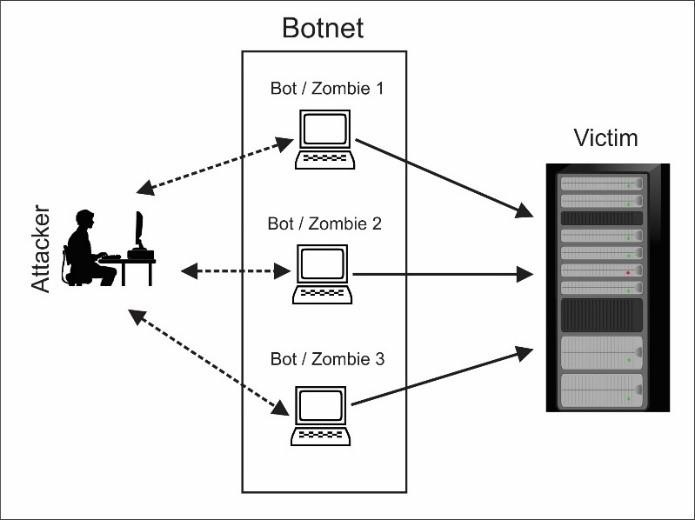
Think of it this way: imagine thousands of people all trying to enter a store through a single door at exactly the same moment. The doorway becomes completely blocked, preventing anyone—including legitimate customers—from getting through. That's essentially what happens to your servers during a DDoS attack, except instead of people, it's millions of automated requests crashing through your digital doors.
Every server and network has a maximum capacity for handling simultaneous requests. When a botnet exceeds that threshold, your systems buckle under the load and crash, leaving your business offline.
The Ransomware Connection
DDoS attacks are increasingly being weaponized as part of broader extortion schemes. Cybercriminals launch DDoS attacks to demonstrate their capabilities, then demand ransom payments to stop the assault. In many cases, the DDoS attack serves as a smokescreen—keeping your security team distracted while attackers deploy ransomware or steal sensitive data through other vulnerabilities.
This layered approach to cybercrime makes comprehensive security measures more critical than ever. Your business needs protection not just against the DDoS attack itself, but also against the secondary threats that may follow.
Why DDoS Protection Matters Now More Than Ever
DDoS attacks have become shorter but larger, with 86.78% of attacks lasting less than 10 minutes in 2024, yet generating a combined 793.4 terabits of malicious traffic. These quick-strike attacks can cripple your infrastructure before your team even realizes what's happening.
The financial stakes are enormous. Beyond the immediate revenue loss from downtime, businesses face long-term damage to customer trust, potential regulatory penalties, and the substantial costs of incident response and recovery.
Understanding the DDoS threat is the first step toward protecting your business. As attack volumes continue their exponential growth trajectory and cybercriminals develop increasingly sophisticated techniques, proactive defense strategies and robust DDoS mitigation solutions have become essential components of any comprehensive cybersecurity program.